3 Information Security Policies To Help Create a Strong Anti-phishing Foundation - CPO Magazine
By A Mystery Man Writer


Phishing Awareness Toolkit

Chapter 3 - Foundations of Security and Loss PreventionSec.docx

The Cyber Defense eMagazine January Edition for 2024

How to Become a CISO (Chief Information Security Officer)

Resources and News, Thought Leadership

Risk Management of the Emerging Tech and Security Landscapes for 2024

💾 Billy Spears - CNBC Technology Executive Council

Cyberespionage accusations. NetScaler backdoors. Phishing scam targets executives. LinkedIn account hijacking. Raccoon Stealer updated. Cryptocurrency recovery scams.
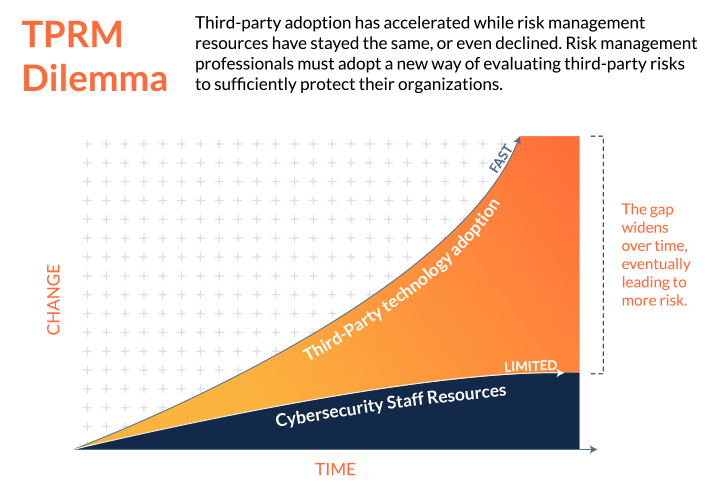
The ONE Thing Third-Party Cyber Risk Management Programs Do